Lonely Hacker MOD APK is a revolutionary tool for tech enthusiasts, providing unique features and benefits for a safe and enjoyable hacking.

Lonely Hacker MOD APK v23.1 (Unlimited Money)
| App Name | The Lonely Hacker |
|---|---|
| Publisher | The Lonely Developer 1987 |
| Genre | Apps, Games |
| Size | 323M |
| Latest Version | 23.1 |
| Get it On |

|
| MOD Info | Unlimited Money |
Lonely Hacker MOD APK is an exciting and innovative tool that has captured the attention of tech enthusiasts around the world. With its unique features and user-friendly interface, this app has become a must-have for anyone interested in exploring the world of hacking. Whether you’re a seasoned pro or just starting out, it provides a safe and enjoyable environment for all your hacking needs. In this blog post, we will take a closer look at what makes it so special, and explore some of the many benefits that it offers to its users.
About Lonely Hacker MOD APK
Lonely Hacker MOD APK is a popular app among tech enthusiasts who are interested in exploring the world of hacking. The app offers a wide range of features and tools that make it easy for users to learn and experiment with hacking in a safe and controlled environment. Whether you’re interested in network penetration testing, website hacking, or just want to explore some of the tools and techniques used by professional hackers, it has something to offer. One of the key benefits of the app is its user-friendly interface. Even if you have little or no experience with hacking, the app makes it easy to get started and provides plenty of guidance and support along the way. With this app, you can experiment with a variety of hacking techniques and tools without having to worry about damaging your own system or breaking any laws. In addition to its user-friendly interface, it also offers a high degree of customization. Users can choose from a variety of themes and settings to create a personalized experience that suits their individual needs and preferences. Whether you prefer a dark or light color scheme, or want to adjust the font size and style, this app makes it easy to customize the app to your liking. It is undoubtedly a versatile and powerful app that has something to offer for anyone interested in hacking or cybersecurity. With its unique features and benefits, it’s no wonder that the app has become so popular among tech enthusiasts around the world.

What Is Lonely Hacker APK?
Lonely Hacker is a fascinating and innovative tool designed for individuals interested in hacking and cybersecurity. The app provides users with a variety of features and tools that make it easy to learn and experiment with hacking in a safe and controlled environment. It offers a unique way to explore the world of hacking without having to worry about damaging your own system or breaking any laws. The app offers a wide range of features, including tools for network penetration testing, website hacking, and much more. With this app, you can learn about a variety of hacking techniques and tools used by professional hackers, and even experiment with them in a safe and controlled environment. One of the key benefits of this app is its user-friendly interface. Even if you have little or no experience with hacking, the app makes it easy to get started and provides plenty of guidance and support along the way. With Lonely Hacker you can learn at your own pace and experiment with a variety of tools and techniques. It is a powerful and versatile tool that has something to offer for anyone interested in exploring the world of hacking and cybersecurity. With its unique features and benefits, the app is quickly becoming a favorite among tech enthusiasts around the world.
User-Friendly Interface
One of the most important features of this app is its user-friendly interface. The app is designed to be easy to use and navigate, even for individuals who have little or no experience with hacking. The interface is intuitive and organized, with clearly labelled menus and options. Users can easily access a variety of tools and techniques without having to navigate through complex menus or instructions. The app also provides plenty of guidance and support for users, with step-by-step instructions and explanations of each tool and technique. This helps to make the learning process smoother and more enjoyable for users of all skill levels. The user-friendly interface of Lonely Hacker makes it a great tool for anyone interested in exploring the world of hacking and cybersecurity.
Customizable Settings
It offers a high degree of customization, with a variety of settings and options that users can adjust to suit their individual needs and preferences. Users can choose from a variety of themes and color schemes, adjust the font size and style, and customize the layout and organization of the interface. In addition, the app allows users to customize the behavior of various tools and techniques, giving them greater control over their hacking experience. This level of customization allows users to tailor the app to their individual needs and preferences, making it a more enjoyable and effective tool for learning and experimentation.
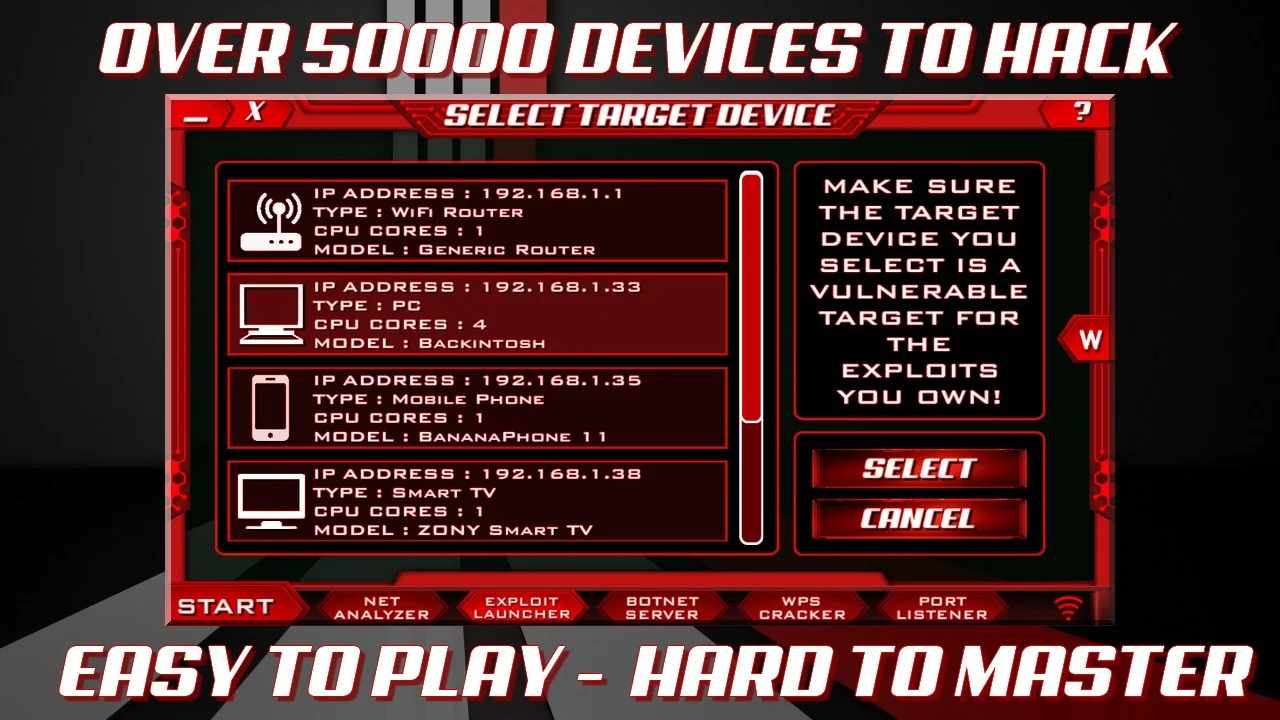
Network Penetration Testing
One of the key features of this app is its network penetration testing tools. With these tools, users can scan and analyse networks to identify potential vulnerabilities and security weaknesses. This can be a valuable tool for organisations and individuals looking to improve their network security and protect against potential threats.The app includes a variety of network penetration testing tools, including port scanning, vulnerability scanning, and packet sniffing. These tools can help users identify open ports, vulnerabilities in network protocols, and potential security threats.
Website Hacking
It also includes a variety of tools and techniques for website hacking. With these tools, users can explore the security of websites and web applications, and identify potential vulnerabilities and security weaknesses. The app includes tools for SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and much more. These tools can help users identify vulnerabilities in websites and web applications, and even exploit those vulnerabilities to gain access to sensitive information or resources.
Social Engineering Tools
It also includes a variety of social engineering tools, which can be used to manipulate individuals or groups in order to gain access to sensitive information or resources. These tools can be valuable for organizations looking to improve their security by training employees to identify and resist social engineering attacks. The app includes a variety of social engineering tools, including keylogging, phishing, and password cracking. These tools can help users learn about the different types of social engineering attacks and how they can be used to gain access to sensitive information or resources.
Keylogging
Keylogging is a technique used by hackers to record the keystrokes entered on a device, such as a computer or smartphone. This can be used to gain access to sensitive information such as passwords, credit card numbers, and other personal data. Lonely Hacker includes a keylogging tool that can be used to monitor and record keystrokes on a target device. This can be a valuable tool for individuals and organizations looking to test their own security by identifying potential vulnerabilities related to keylogging.
Password Cracking
Password cracking is a technique used by hackers to gain access to password-protected accounts or systems. It involves using automated tools to generate a large number of possible passwords until the correct password is identified. IT includes a password cracking tool that can be used to test the strength of passwords and identify potential vulnerabilities. Users can specify the parameters of the password, such as length, character sets, and complexity, to generate a list of possible passwords that can be tested against a target account or system.
Vulnerability Scanning
Vulnerability scanning is the process of identifying potential security vulnerabilities in a system or network. This can involve scanning for open ports, known vulnerabilities in software, or other potential weaknesses. It includes a variety of vulnerability scanning tools, including port scanning and vulnerability scanning. These tools can help users identify potential vulnerabilities in a network or system, and take steps to mitigate or eliminate those vulnerabilities.
Packet Sniffing
Packet sniffing is the process of intercepting and analyzing network traffic in order to identify potential security threats or vulnerabilities. This can involve monitoring network traffic for unusual or suspicious activity, or analyzing packet headers and payloads for potential weaknesses. It includes a packet sniffing tool that can be used to intercept and analyze network traffic. This can be a valuable tool for individuals and organizations looking to test their own security, or identify potential threats on a network.
Port Scanning
Port scanning is the process of scanning a network for open ports. This can be a valuable tool for identifying potential vulnerabilities in a network, as open ports can provide access points for attackers. It includes a port scanning tool that can be used to scan a network for open ports. Users can specify the range of ports to be scanned, and the tool will return a list of open ports on the network. This information can be used to identify potential vulnerabilities, and take steps to close or secure those ports.
Exploitation Tools
Exploitation tools are used by hackers to take advantage of vulnerabilities in software or systems. These tools allow attackers to gain unauthorized access to a system, steal data, or cause other damage. It includes a range of exploitation tools that can be used to identify and exploit vulnerabilities in software and systems. These tools include buffer overflow exploits, SQL injection exploits, and other techniques for exploiting weaknesses in a target system.
Remote Access Tools
Remote access tools allow users to control a target device from a remote location. These tools can be used for legitimate purposes, such as IT support, but can also be used by hackers to gain unauthorized access to a system. It includes a range of remote access tools that can be used to control a target device remotely. These tools can be used for testing purposes, or by security professionals to identify and mitigate potential vulnerabilities in a system.
Malware Creation And Analysis
Malware is software designed to cause damage to a system or steal sensitive data. Malware creation and analysis tools allow users to create and test malware, and to analyze existing malware to identify potential weaknesses. It includes a range of malware creation and analysis tools. These tools can be used to create and test malware, or to analyze existing malware to identify potential weaknesses and improve the security of a system.
Cryptography Tools
Cryptography is the science of encrypting and decrypting information. Cryptography tools allow users to encrypt and decrypt data to protect it from unauthorized access. It includes a range of cryptography tools that can be used to encrypt and decrypt data. These tools can be used for testing purposes, or by security professionals to protect sensitive data and ensure the security of a system.

Forensic Analysis Tools
Forensic analysis tools are used to investigate and analyze digital evidence related to a cybercrime. These tools can be used to identify the source of an attack, recover deleted data, and analyze other digital evidence. It includes a range of forensic analysis tools that can be used to investigate and analyze digital evidence related to a cybercrime. These tools can be used by law enforcement agencies, cybersecurity professionals, and other investigators to identify and prosecute cybercriminals, and to improve the security of computer systems and networks.
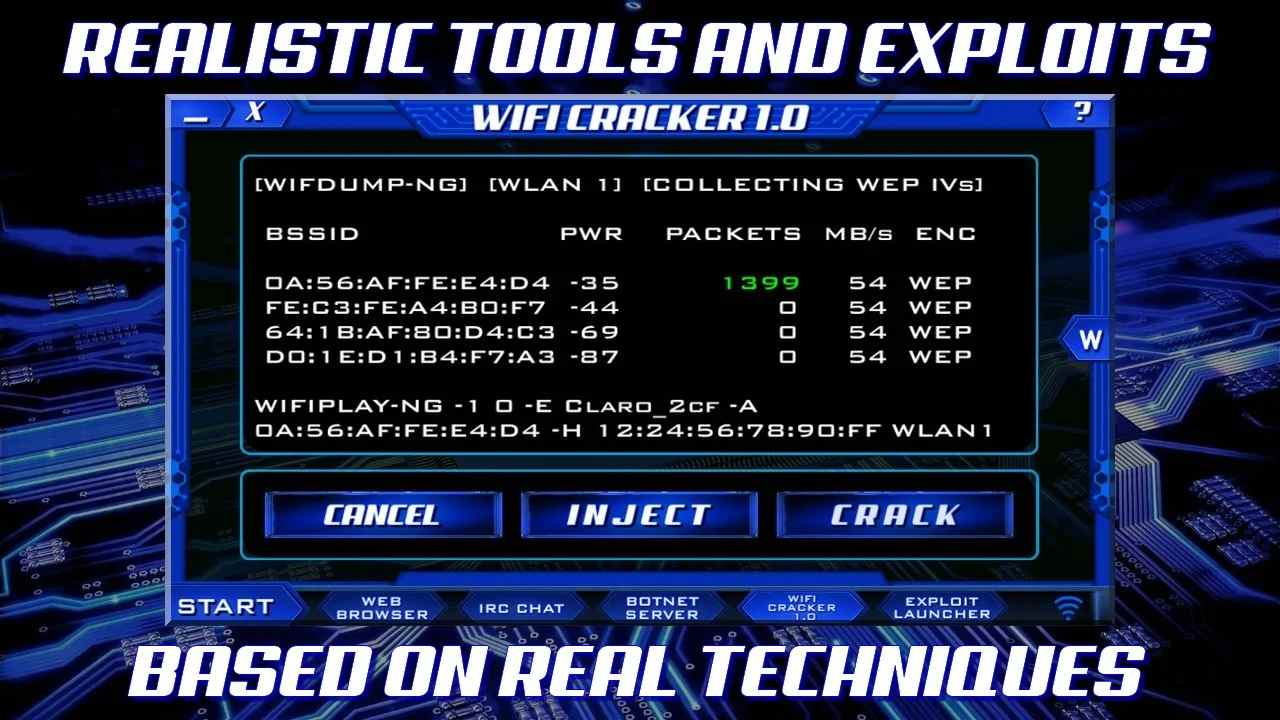
Wi-Fi Hacking Tools
Wi-Fi hacking tools allow users to hack into wireless networks and access their data. These tools can be used to gain unauthorized access to a Wi-Fi network, monitor network traffic, or intercept data being transmitted over the network. It includes a range of Wi-Fi hacking tools that can be used to test the security of wireless networks. These tools can be used to identify vulnerabilities in a Wi-Fi network and improve its security.
Brute Force Attacks
Brute force attacks are a type of hacking attack that involves attempting to guess a password by trying every possible combination of characters. These attacks can be used to gain unauthorized access to a system or account. It includes a range of tools that can be used to perform brute force attacks on passwords. These tools can be used for testing purposes, or by security professionals to identify potential weaknesses in a system.
SQL Injection Tools
SQL injection attacks are a type of hacking attack that involves inserting malicious code into a SQL database query. These attacks can be used to gain unauthorized access to a database, steal sensitive data, or cause other damage. It includes a range of SQL injection tools that can be used to test the security of a database. These tools can be used to identify potential vulnerabilities in a database and improve its security.
XSS (Cross-Site Scripting) Tools
Cross-site scripting (XSS) attacks are a type of hacking attack that involves injecting malicious code into a website. These attacks can be used to steal sensitive data or cause other damage. It includes a range of XSS tools that can be used to test the security of a website. These tools can be used to identify potential vulnerabilities in a website and improve its security.
CSRF (Cross-Site Request Forgery) Tools
Cross-site request forgery (CSRF) attacks are a type of hacking attack that involves tricking a user into making a request on a website without their knowledge. These attacks can be used to steal sensitive data or cause other damage. It includes a range of CSRF tools that can be used to test the security of a website. These tools can be used to identify potential vulnerabilities in a website and improve its security.
CSRF Pock (Proof Of Concept) Generator
A CSRF Pock (Proof of concept) generator is a tool that can be used to create a proof-of-concept attack for a Cross-Site Request Forgery (CSRF) vulnerability. The generator can be used to demonstrate how an attacker could exploit the vulnerability to execute a malicious action on a website. It includes a CSRF Pock generator that allows security professionals to test the security of a website by creating and executing a CSRF attack.
CSRF Tester
A CSRF tester is a tool that can be used to test the security of a website for Cross-Site Request Forgery (CSRF) vulnerabilities. The tester can be used to identify vulnerabilities that could be exploited by attackers to execute malicious actions on the website. It includes a CSRF tester that allows security professionals to test the security of a website for CSRF vulnerabilities. The tester can be used to identify and remediate potential vulnerabilities to improve the overall security of the website.
Custom Exploit Generator
A custom exploit generator is a tool that can be used to create a custom exploit for a vulnerability in a system or application. The generator can be used to create an exploit that is specifically tailored to the vulnerability, making it more effective than a generic exploit. It includes a custom exploit generator that allows security professionals to create custom exploits for vulnerabilities in systems and applications. This tool can be used to create more effective exploits that can be used to test the security of a system or application.
Custom payload Generator
A custom payload generator is a tool that can be used to create a custom payload for a vulnerability in a system or application. The payload can be used to execute a specific action or exploit a specific vulnerability. It includes a custom payload generator that allows security professionals to create custom payloads for vulnerabilities in systems and applications. This tool can be used to create more effective payloads that can be used to test the security of a system or application.
Custom Script Executor
A custom script executor is a tool that can be used to execute custom scripts on a system or application. The executor can be used to automate tasks or perform actions that are not supported by the system or application. It includes a custom script executor that allows security professionals to execute custom scripts on systems and applications. This tool can be used to automate tasks, perform advanced actions, or test the security of a system or application.
Conclusion
Lonely Hacker is a comprehensive and powerful tool for security professionals who want to test the security of systems and applications. With a user-friendly interface, customizable settings, and a wide range of features, it offers a complete solution for security testing. The tool provides a range of capabilities, from network penetration testing and website hacking to social engineering and forensics analysis. Its wide range of features includes keylogging, password cracking, vulnerability scanning, packet sniffing, port scanning, and many others. It is a valuable resource for security professionals who want to test and improve the security of systems and applications. However, it is important to note that the tool should only be used for ethical and legal purposes. As with any tool, it can be misused by malicious actors for illegal or unethical activities. It is no doubt a powerful and useful tool for security professionals, and its wide range of features and capabilities make it a valuable asset in the field of security testing.





